Ever sent something important, like a private letter, expecting it to go straight from you to the intended recipient? Now, imagine someone sneaky intercepts that letter mid-journey, steams it open, reads everything inside (maybe even makes a few tiny changes!), and then carefully seals it back up before sending it on its way. The person you sent it to never knows it was compromised.
Creepy, right? Well, in the digital world, this unsettling scenario has a name: the Man-in-the-Middle (MITM) attack. It’s a deceptively simple yet incredibly dangerous form of cyberattack where a malicious party inserts themselves directly into a seemingly private conversation or data exchange between two unsuspecting systems or individuals.
Table of Contents
Understanding the “Man in the Middle” Concept
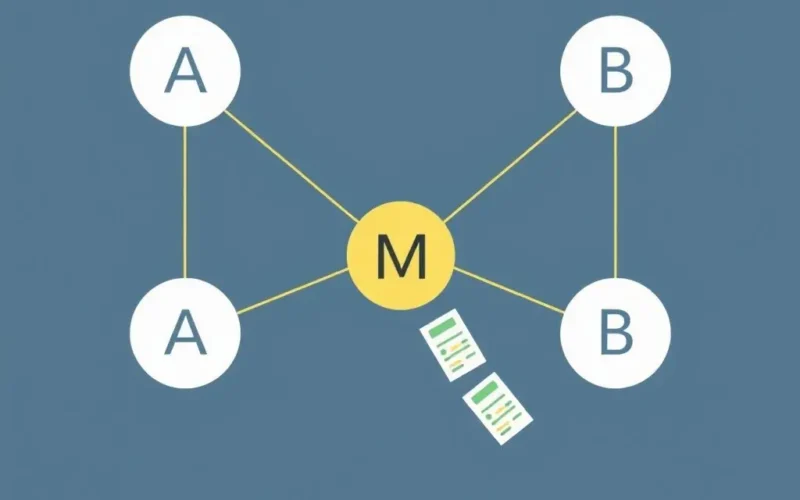
At its core, a MITM attack is all about unauthorized interception. Think of any online communication – you browsing your bank’s website, you sending an email, your phone connecting to a public Wi-Fi hotspot, or even your smart device talking to a server. Data packets are constantly flowing back and forth.
A “man in the middle” (who could be a single person, a group, or automated software) positions themselves on the network path between you and the service you’re trying to reach. They become an unauthorized relay point. Instead of your data going directly from Point A to Point B, it gets rerouted through Point M (the middle), where the attacker can listen, read, and potentially tamper with the information before forwarding it.

How Do Attackers Get Into the Middle?
Becoming the intermediary isn’t always easy, but attackers use various techniques to position themselves strategically:
- Public Wi-Fi Exploits: Unsecured or poorly configured public Wi-Fi networks are prime targets. Attackers can set up rogue hotspots or exploit vulnerabilities in legitimate ones to intercept traffic from connected devices.
- ARP Spoofing: On a local network (like your home or office network), Address Resolution Protocol (ARP) spoofing involves tricking devices into sending their network traffic to the attacker’s machine instead of the legitimate gateway or router.
- DNS Spoofing: Domain Name System (DNS) spoofing involves redirecting your request for a website (like yourbank.com) to a fake, malicious website controlled by the attacker, even if you typed the correct address.
- SSL Stripping: This attack downgrades a secure HTTPS connection to an insecure HTTP connection without your knowledge. While you might see “http” (or nothing, depending on the browser), the attacker maintains an HTTPS connection with the legitimate site while communicating with you over the vulnerable HTTP channel, allowing them to see everything in plain text.
- Malware: Certain types of malware installed on your device or a router can act as the “man in the middle,” intercepting data before it even leaves your system or as it passes through your local network equipment.
- Session Hijacking: Stealing a user’s session cookies or tokens to take control of their active session with a web application.
The goal is always the same: position the attacker’s device or software as the crucial bridge (or blockade) that all traffic must cross.
Visualizing the Digital Hijack: What Data is at Risk?
When a MITM attack is successful, the attacker gains terrifying visibility into the data flowing between you and the online service. Imagine those digital packets of information as miniature envelopes. In a secure, uncompromised connection, these envelopes are sealed and perhaps encrypted, going directly to their destination.
In a MITM scenario, the attacker is sitting at the post office, opening every envelope addressed to or from you. What might they find?
- Login Credentials: Usernames and passwords for websites, email accounts, social media, etc.
- Financial Information: Credit card numbers, bank account details, transaction data.
- Personal Identifiable Information (PII): Names, addresses, birthdates, passport details, etc.
- Private Communications: Emails, chat messages, even potentially voice calls depending on the protocol.
- Sensitive Documents: Any files being uploaded or downloaded.
Not only can they see this data, but in many cases, they can also alter it. Think about a financial transaction – the attacker could potentially change the recipient’s account number or the amount before forwarding the request to the bank, leading to fraudulent transfers.

Want a quick visual rundown of this whole data interception business? We put together a short video that illustrates the core concept:
Why MITM Attacks Pose a Significant Threat
The danger of MITM attacks isn’t just about data theft; it’s about the complete subversion of trust in a digital interaction. Because the attacker is literally *in the flow*, they can:
- Steal Sensitive Information: Leading to identity theft, financial fraud, and account takeover.
- Alter Data: Corrupting files, changing transaction details, or injecting malicious links or code into legitimate web pages you’re viewing.
- Plant Malware: Redirecting you to malicious download sites or injecting malicious software directly into software updates or downloads.
- Eavesdrop on Communications: Gaining access to private conversations and proprietary business information.
- Remain Undetected: If done skillfully (especially with SSL stripping), the user might have no visual indication that their connection has been compromised.

Protecting Your Digital Conversations
Fortunately, there are steps you can take to significantly reduce your risk of falling victim to a MITM attack:
- Always Use HTTPS: Look for “https://” at the beginning of a website’s address and a padlock icon in your browser bar. HTTPS encrypts the connection between your browser and the website server, making it incredibly difficult for an attacker in the middle to read the data. Be wary of browser warnings about insecure certificates.
- Be Cautious on Public Wi-Fi: Avoid conducting sensitive activities like banking, shopping, or logging into important accounts on public Wi-Fi networks. If you must use public Wi-Fi, use a Virtual Private Network (VPN).
- Use a VPN (Virtual Private Network): A VPN encrypts your entire internet connection, routing it through a secure server. This creates a secure tunnel that makes it much harder for anyone on the local network (like public Wi-Fi) or along the path to intercept your data.
- Keep Software Updated: Regularly update your operating system, web browsers, and security software. Updates often patch vulnerabilities that MITM attackers exploit.
- Use Strong, Unique Passwords & Multi-Factor Authentication (MFA): Even if credentials are intercepted, MFA makes it harder for attackers to log in.
- Disable Automatic Wi-Fi Connection: Configure your devices not to automatically connect to known Wi-Fi networks, especially public ones. Manually choose trusted networks.
- Be Suspicious of URLs: Double-check website addresses for misspellings or slight variations, especially if you arrived there via a link.

Frequently Asked Questions (FAQs) About MITM Attacks
Got more questions about these tricky attacks? Here are some common ones:
Q1: Can a MITM attack happen on my home network?
A: Yes. While public Wi-Fi is a common vector, MITM attacks like ARP spoofing or DNS spoofing can occur on a compromised home network, especially if your router has weak security or is infected with malware.
Q2: Does using a strong password protect against MITM?
A: A strong password is essential for overall security, but it won’t prevent a MITM attacker from intercepting your password if the connection isn’t encrypted (like on HTTP) or if they use techniques like SSL stripping. It helps prevent unauthorized access *if* they get the password, but the goal is to prevent them from seeing it in the first place.
Q3: How can I tell if I’m a victim of a MITM attack?
A: Detecting a MITM attack can be very difficult, as they are designed to be stealthy. Warning signs *might* include unexpected browser security warnings (especially about certificates), unusually slow connections to specific websites, or unexpected redirects. However, many sophisticated attacks leave no obvious trace for the average user. Relying on protective measures like HTTPS, VPNs, and security software is key.
Q4: Is encryption enough to stop MITM?
A: Encryption, especially through HTTPS and VPNs, is the primary defense against MITM attacks that aim to read or alter data in transit. However, attackers can target the *setup* of the encrypted connection (like with SSL stripping) or intercept data *before* it’s encrypted (if malware is on your device). So, while critical, encryption is most effective as part of a layered security approach.
Staying Vigilant in the Digital Realm
Understanding how Man-in-the-Middle attacks work isn’t about creating fear; it’s about empowering yourself with knowledge. By recognizing the potential risks and adopting simple but effective security habits – like checking for HTTPS, being mindful of public Wi-Fi, and using a VPN – you can significantly strengthen your defenses against these invisible digital eavesdroppers. Protecting your data flow is a crucial step in navigating the online world securely.