Imagine your computer, your home network, or even your entire business network as a precious stronghold, a digital fortress filled with valuable data, important files, and sensitive information. Now, how do you protect this valuable digital real estate from the ever-present threats lurking in the vast, wild frontier of the internet?
Just as a medieval castle needed robust walls and a guarded gate to keep invaders out while allowing allies in, your digital fortress requires a similar line of defense. In the realm of cybersecurity, this critical guardian is known as a firewall.
Curious to see this concept brought to life in a quick, engaging way? Check out our YouTube Shorts video that perfectly captures the essence of a firewall using this very metaphor. It might just clear up any digital fog!
Table of Contents
What Exactly *Is* a Firewall?
Stripping away the metaphors for a moment, a firewall is essentially a network security device or software program that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Think of it as the crucial checkpoint between your trusted internal network and untrusted external networks, like the internet.
Its primary job is to decide whether specific network traffic should be allowed to pass through or be blocked, all based on a set of established security policies. This filtering process helps prevent unauthorized access, malicious attacks, and the entry of harmful software like malware.
The Brick Wall Metaphor, Unpacked
Let’s revisit our fortress analogy, as it’s incredibly helpful for understanding how firewalls function:
- The Brick Wall: This represents the protective barrier a firewall creates around your network. It’s not just a passive wall; it actively inspects everything attempting to cross it.
- The Gate: This is the controlled entry/exit point. Data doesn’t just flow freely; it must pass through the gate where it’s examined.
- The Bouncer/Guard: This is the core function of the firewall software/hardware. It’s the entity performing the inspection at the gate. It checks the ‘credentials’ of incoming (and sometimes outgoing) data packets.
- The Security Rules: These are the instructions the bouncer follows. Rules might be based on the source IP address, destination IP address, port number, type of protocol (like HTTP, HTTPS, FTP), or even the content of the packet itself (in more advanced firewalls).
If a data packet follows the rules (e.g., it’s from a trusted source, destined for an allowed service), the bouncer opens the gate. If it looks suspicious, violates a rule, or is specifically on a ‘deny’ list, it’s politely (or sometimes abruptly) blocked and turned away.

Why Do You Need This Digital Wall?
In today’s interconnected world, being online means being exposed to potential threats. A firewall acts as your first line of defense against a multitude of digital dangers:
- Unauthorized Access Attempts: Hackers constantly scan networks looking for vulnerabilities to exploit. A firewall can block these scanning attempts and prevent unauthorized logins.
- Malware and Viruses: While antivirus software catches malicious programs already on your system, a firewall can prevent malware from entering your network in the first place by blocking connections to known malicious sites or ports.
- Denial-of-Service (DoS) Attacks: Firewalls can help mitigate some DoS attacks by identifying and blocking traffic floods from malicious sources.
- Data Theft: By controlling which applications and services can send data out, firewalls can help prevent sensitive information from being illicitly transmitted from your network.
- Policy Enforcement: In business settings, firewalls can enforce organizational policies, like blocking access to certain websites or restricting the use of specific applications.
Different Kinds of Digital Walls
Firewalls aren’t one-size-fits-all. They come in various forms, each with different capabilities and levels of inspection:
- Packet-Filtering Firewalls: The most basic type. They examine packets individually, checking source/destination IP and port numbers against a set of rules. Simple but can be vulnerable to certain attacks as they don’t inspect the packet’s context.
- Stateful Inspection Firewalls: More advanced. They not only check individual packets but also keep track of the ‘state’ of active connections. This allows them to make more intelligent decisions based on whether a packet is part of a legitimate, ongoing conversation.
- Proxy Firewalls (Application-Level Gateways): These act as intermediaries for specific types of application traffic (like web traffic). They inspect the content of packets more deeply, offering greater security but potentially impacting performance.
- Next-Generation Firewalls (NGFWs): These combine traditional firewall functions with advanced features like intrusion prevention systems (IPS), application control, and threat intelligence feeds. They offer much deeper inspection and control.
Firewalls can also be categorized by where they are deployed:
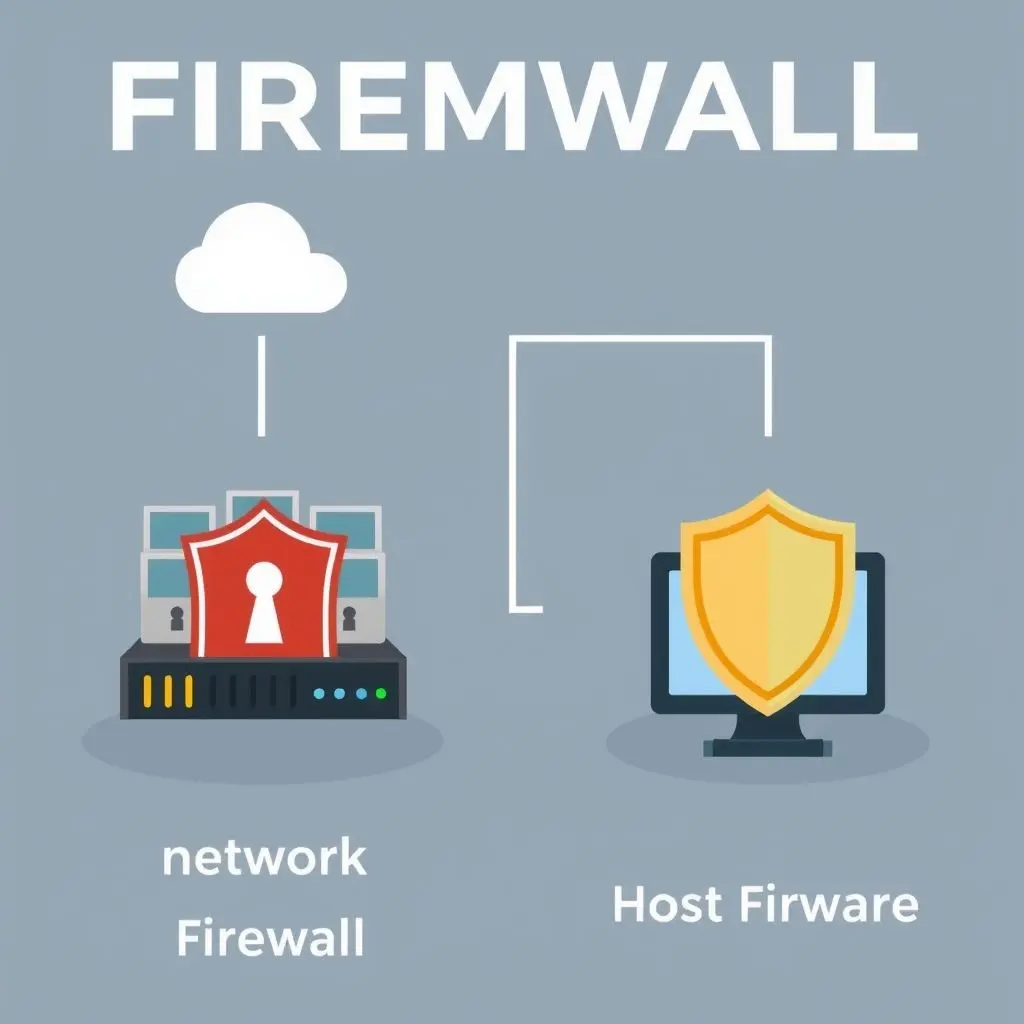
- Network-Based Firewalls: These are often hardware devices placed at the gateway of a network (e.g., between your router and the internet). They protect the entire network behind them.
- Host-Based Firewalls: These are software applications installed on individual computers or servers. They protect only the host they are installed on and can be customized for specific machine needs (like the built-in firewalls in Windows or macOS).
Building the Rules: How Firewalls Decide
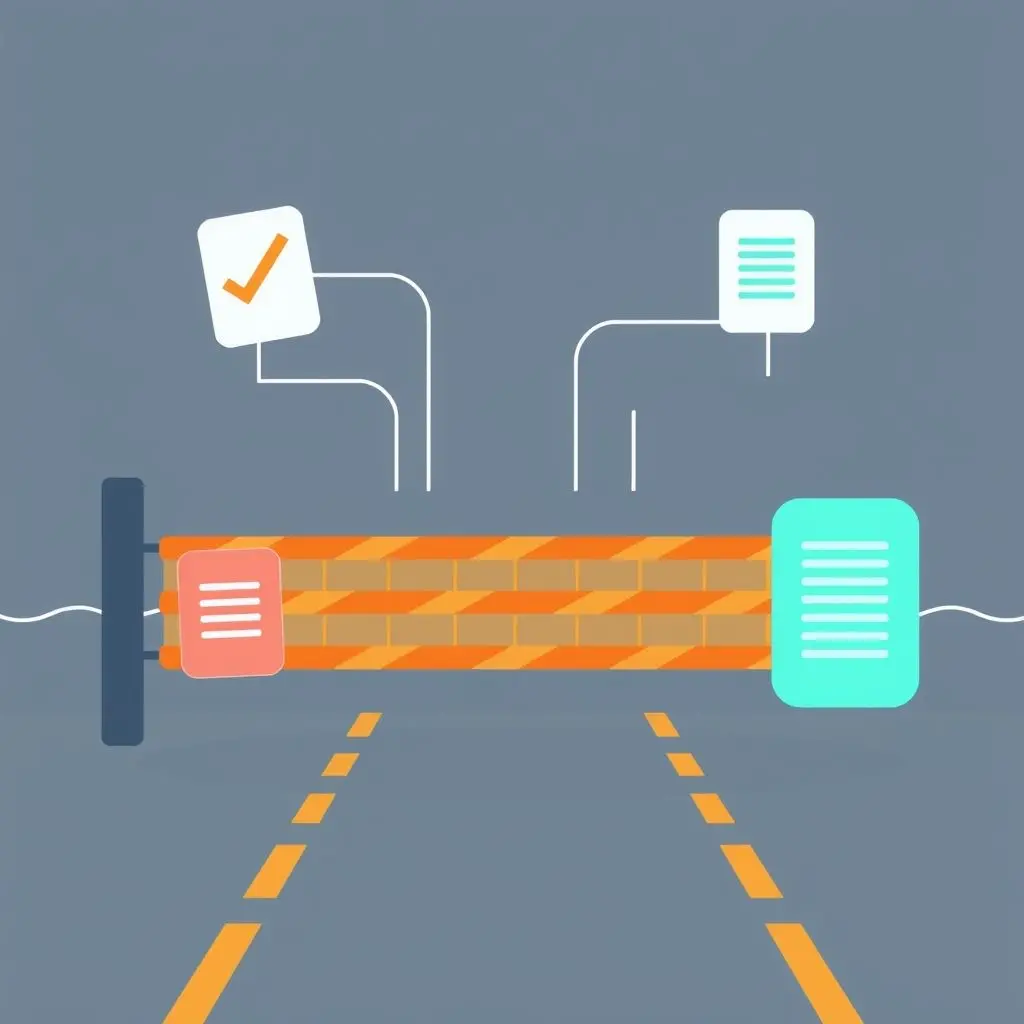
The effectiveness of a firewall heavily relies on its ruleset or policy. These rules are configured by administrators and dictate what traffic is permitted or denied. A typical rule might look something like this:
Allow all incoming traffic on port 80 (HTTP) and 443 (HTTPS) to the web server’s IP address.
Or conversely:
Deny all incoming traffic from a specific known malicious IP address range.
Rules are usually processed in order, with the first matching rule determining the action. A poorly configured firewall, even a sophisticated one, can leave glaring security holes.
More Than Just a Wall
While a firewall is a cornerstone of digital defense, it’s important to remember it’s not the *only* security measure you need. A complete security strategy includes antivirus software, intrusion detection/prevention systems (often integrated into NGFWs), regular software updates (patching vulnerabilities), strong passwords, and crucially, user education about safe online practices.
Think of it as adding more layers to your fortress’s defense – guards patrolling the grounds, secure locks on doors, and well-trained inhabitants.
Frequently Asked Questions About Firewalls
Q: Do I need a firewall if I already have antivirus software?
A: Yes, absolutely. They serve different purposes. Antivirus software scans for, detects, and removes malicious software on your system. A firewall controls network traffic, preventing threats from reaching your system in the first place.
Q: Is the firewall built into my router or operating system enough?
A: For basic home use, the firewalls included in your router and operating system (like Windows Firewall or macOS Firewall) provide a foundational level of protection. However, for businesses or users dealing with sensitive data, a more robust, dedicated firewall solution (like a next-generation firewall appliance) is often recommended for enhanced features and centralized management.
Q: Can a firewall protect me from *all* online threats?
A: No firewall can offer 100% protection. New threats and techniques emerge constantly. A firewall is a critical component, but it works best as part of a comprehensive security approach that includes other security software, regular updates, and cautious online behavior.
Q: Does a firewall slow down my internet connection?
A: Simple packet-filtering firewalls typically have minimal impact. More advanced firewalls, like stateful inspection or proxy firewalls that perform deeper packet inspection, can introduce a small amount of latency or overhead. However, modern firewalls are designed to be highly efficient, and any noticeable slowdown is often negligible for everyday tasks, especially if the hardware is appropriately sized for the network traffic.
Q: What’s the difference between a hardware and software firewall?
A: A hardware firewall is a physical appliance (like a router or dedicated security device) that sits between your network and the external connection. A software firewall is a program installed on a computer or server. Hardware firewalls protect entire networks, while software firewalls protect individual devices.
Keeping Your Digital Gates Guarded
In essence, a firewall is your network’s vigilant guardian, standing watch at the gate, meticulously examining every piece of digital traffic. It’s an indispensable part of any modern cybersecurity strategy, providing that essential layer of defense that keeps the bad stuff out and your important stuff safe inside your digital fortress. Understanding its role is the first step in fortifying your online presence effectively.



