Ever wonder about the digital ghost trick VPNs pull off? You know, the one where they make it look like you’re browsing from a cozy cafe in Paris when you’re actually chilling on your couch? It all comes down to how they handle your IP address, that unique numerical tag that essentially tells the internet where you are.
Think of your IP address like your home address for the digital world. Every time you connect to a website or online service, your device sends out requests, and your IP address is attached so the information knows where to return. It’s essential for the internet to function, but it also reveals a fair bit about you – your general location, your internet provider, and potentially even helps track your online activity.
Table of Contents
Why Bother Hiding Your IP Address?
There are several compelling reasons why people opt to conceal their digital footprint:
- Privacy: Prevent websites, advertisers, and other third parties from tracking your online movements and building detailed profiles based on your browsing habits and location.
- Security: While hiding your IP isn’t a bulletproof security measure on its own, it adds a layer of anonymity that can deter some types of targeted cyber threats.
- Access Geo-Restricted Content: Websites and streaming services often restrict access based on geographical location. By using a VPN server in a different country, you can appear to be accessing the internet from there, potentially unlocking content unavailable in your real location.
- Avoid Censorship: In regions with strict internet censorship, changing your perceived location can help bypass government blocks on certain websites or services.
- Prevent ISP Snooping: Your Internet Service Provider (ISP) can see your online activity linked to your IP address. Using a VPN encrypts your traffic, making it unreadable to your ISP, even if they see you’re connected to the VPN server.
The Secret Sauce: The VPN Tunnel
So, how exactly does a VPN perform this digital vanishing act? The core mechanism is something called an encrypted tunnel.
When you connect to a VPN service, your VPN client software on your device creates a secure, encrypted connection to a VPN server operated by your VPN provider. All the data leaving your device that is routed through the VPN is scrambled (encrypted) before it enters the public internet.
Imagine sending a letter, but instead of just putting it in an envelope, you put it inside a locked box, and only the recipient (the VPN server) has the key. Even if someone intercepts the box (your data packet), they can’t read the contents without the key (the encryption key).

The IP Address Swap: How the Server Takes Over
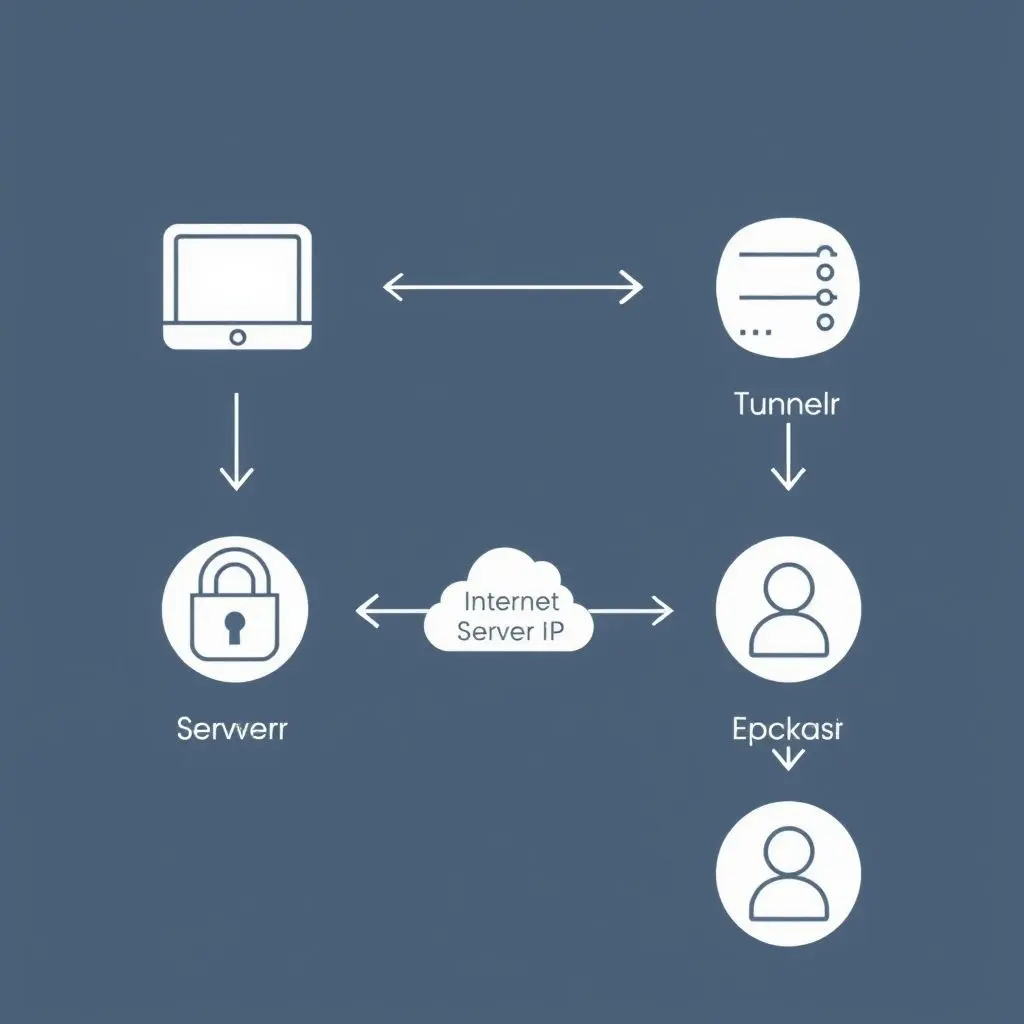
Here’s where your IP address goes into hiding. Your encrypted traffic doesn’t travel directly from your device to the website you want to visit. Instead, it first travels through that secure tunnel all the way to the VPN server.
Once your traffic reaches the VPN server, the server decrypts it. Then, and this is the crucial part, the VPN server sends the request onwards to the final destination (the website, streaming service, etc.) using its own IP address. The website receives the request and sees the VPN server’s IP address as the origin point, not yours.
When the website sends data back (like the webpage content), it sends it to the VPN server’s IP address. The VPN server receives this data, encrypts it again, and sends it back to your device through the secure tunnel. Your VPN client on your device receives the encrypted data and decrypts it for you to see.
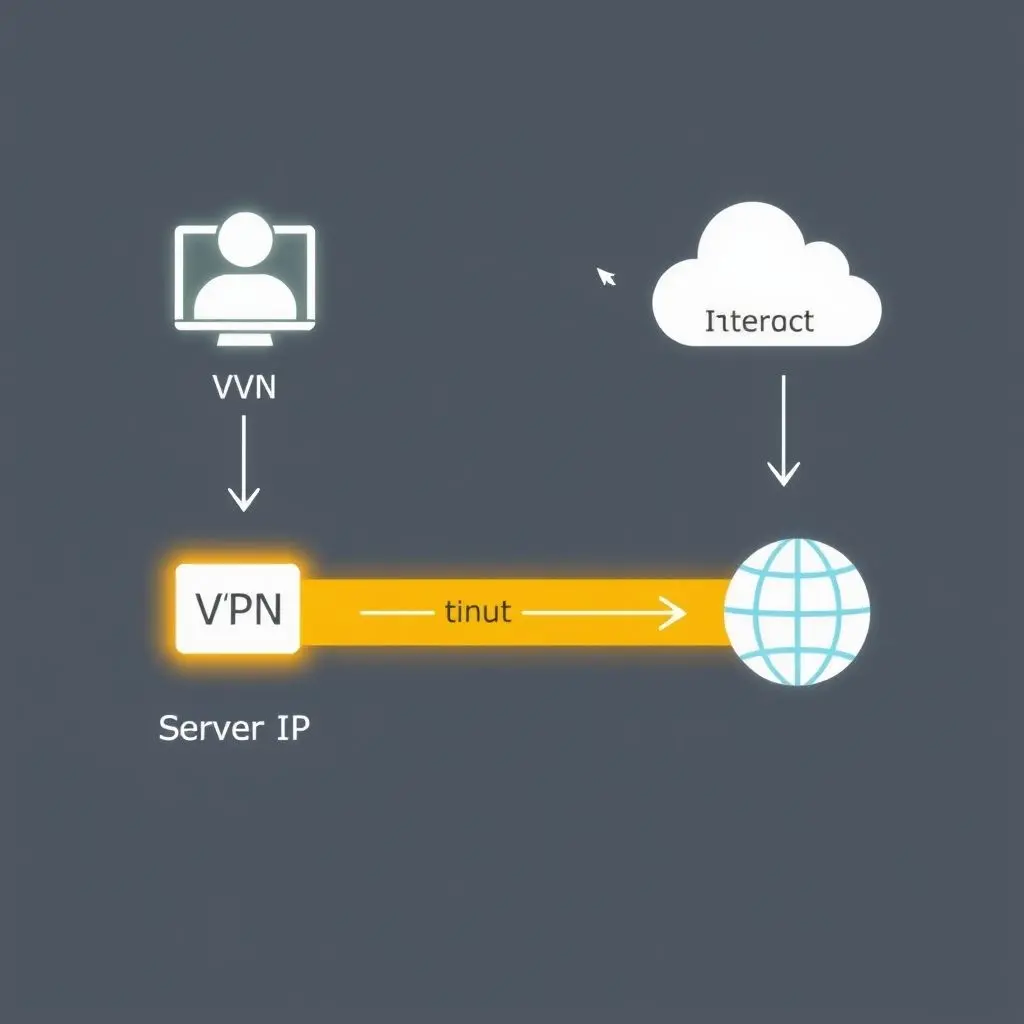
To the outside world – the websites you visit, the online services you use, potential trackers – your real IP address is hidden. They only see the IP address of the VPN server you’re connected to. It effectively acts as a proxy, but with the added benefit of encryption.
This is why choosing a VPN provider with servers in many different locations is beneficial. By connecting to a server in, say, Germany, any website you visit will think you are browsing from Germany, regardless of where you actually are physically.
The Process Step-by-Step
Let’s break down the journey your online request takes:
- You Initiate a Request: You type a website address into your browser or open an app.
- VPN Client Intercepts: Your VPN software on your device is active. It intercepts this outgoing request.
- Encryption: The VPN client encrypts the request data.
- Tunnel Travel: The encrypted data is sent through the secure tunnel across the internet to the chosen VPN server.
- VPN Server Receives & Decrypts: The VPN server receives the encrypted data and decrypts it using the shared key.
- Server Sends Request (with its IP): The VPN server sends the now-decrypted request to the destination website/service using the server’s IP address.
- Website Responds: The website processes the request and sends the response back to the VPN server’s IP address.
- VPN Server Receives & Encrypts: The VPN server receives the response data and encrypts it.
- Tunnel Return: The encrypted response travels back through the tunnel to your device.
- VPN Client Decrypts: Your VPN client receives the encrypted response and decrypts it.
- You See the Result: Your browser or app receives the decrypted data, and you see the requested webpage or content.
Throughout this entire back-and-forth, your original IP address never leaves the secure environment between your device and the VPN server.