Ever pick up a new pair of wireless earbuds or a Bluetooth speaker and wonder how your phone just… knows they’re there, ready to connect? It seems almost magical, this invisible link forming between your devices. That ‘magic’ is actually a carefully orchestrated process called Bluetooth pairing. Think of it as a digital first date, where your gadgets learn to recognize and trust each other.
Let’s peel back the curtain and see what really goes down when you tap ‘Pair’ on your screen. It’s a bit more involved than a simple handshake; it’s a sophisticated security and connection dance.
But before we dive deep, perhaps a quick visual explanation would help set the stage? We put together a short video explaining the basic steps. Check it out below!
Alright, video watched? Let’s get into the nitty-gritty details of this fascinating process.
Table of Contents
Why Pairing? Can’t Devices Just Connect?
You might think, if Bluetooth devices broadcast signals, why can’t any phone just connect to any speaker it finds? The answer boils down to security and dedicated functionality. Pairing creates a secure, dedicated connection between specific devices. Without it, your neighbor could blast their questionable music through your living room speaker, or someone could potentially intercept data flowing between your phone and a medical device.
Pairing establishes a trusted relationship, ensuring that only authorized devices can communicate and share information or audio streams securely.
The Core Steps of Bluetooth Pairing Explained
While the specific interface might vary slightly depending on your device (phone, laptop, speaker, etc.) and the Bluetooth version, the underlying principles of pairing involve a few critical stages:
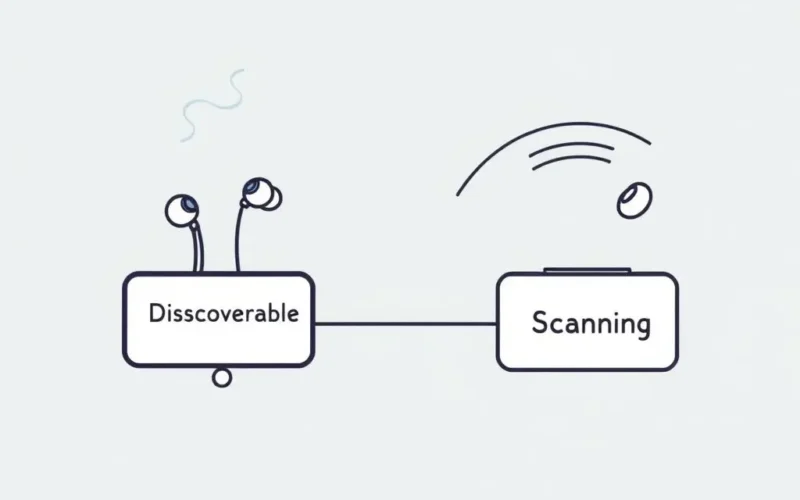
Step 1: Discovery Mode (Making Yourself Visible)
For two Bluetooth devices to find each other, at least one needs to be in ‘discoverable’ mode (sometimes called ‘pairing mode’). Think of this device as actively announcing its presence to the world. It broadcasts specific inquiry access codes (IACs) and device information over dedicated Bluetooth inquiry scan frequencies (usually in the 2.4 GHz band, hopped across channels).
- How to activate: This usually involves pressing and holding a dedicated Bluetooth or power button on the device (like earbuds or a speaker) until an LED starts flashing in a specific pattern or the device plays an audible cue. Consult your device’s manual for the exact method.
- Purpose: To allow other Bluetooth devices that are scanning to detect its presence and identity.
Step 2: Scanning (Looking for Connections)
While one device is discoverable, the other device (like your phone or computer) needs to be actively scanning. It listens for the inquiry signals being broadcast by discoverable devices within its range. Your phone’s Bluetooth settings screen often shows a list of nearby devices it has detected during a scan.
- How to activate: Simply turning on Bluetooth on your phone or computer usually initiates a scan. Refreshing the list of available devices in the Bluetooth settings performs a new scan.
- Purpose: To find and identify discoverable Bluetooth devices nearby.
Once your scanning device detects a discoverable device, it retrieves basic information about it, such as its Bluetooth address (a unique identifier, similar to a MAC address for Wi-Fi) and sometimes its name and the services it offers (like audio streaming). This is when you see the device pop up in the list on your phone screen.
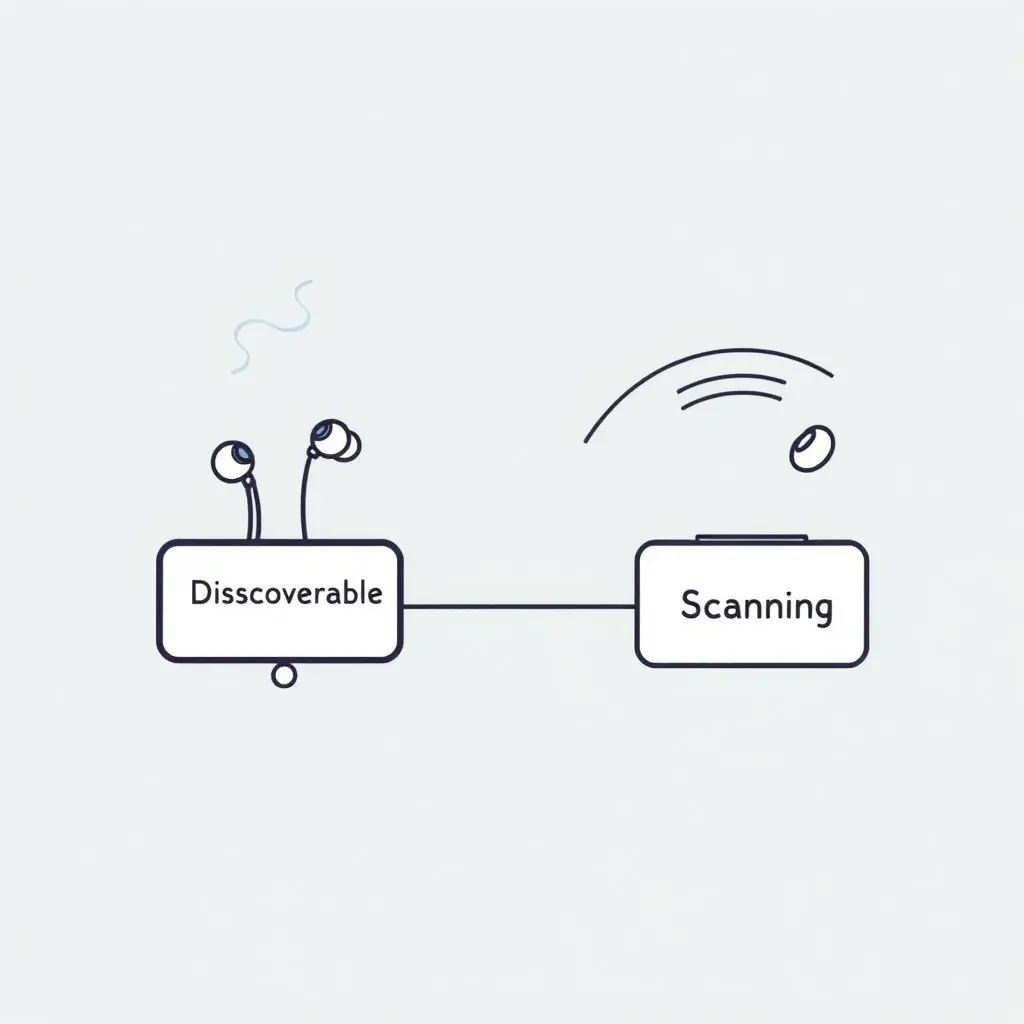
Step 3: Connection Request & Initial Handshake
When you select the discovered device from the list on your phone (e.g., clicking on “My Cool Earbuds”), your phone initiates a connection request. It attempts to establish a temporary, unauthenticated connection with the discoverable device. This is where a basic handshake occurs, exchanging initial parameters and establishing a common communication channel.
At this stage, the devices might start exchanging information required for the next crucial step: authentication and bonding.
Step 4: Authentication & Bonding (The Secure Link)
This is arguably the most critical part for establishing a secure, lasting connection. The goal is to authenticate that both devices are authorized to connect and then create a ‘bond’ so they remember each other for future connections.
Different methods exist for authentication, depending on the Bluetooth version and device capabilities:
Older Methods: PIN Entry (Legacy Pairing)
In older Bluetooth versions (prior to 2.1), pairing often required entering a Personal Identification Number (PIN). This could be a fixed PIN (like “0000” or “1234” for simple devices) or a variable PIN shown on one device to be entered on the other. While seemingly simple, this method had security vulnerabilities, especially with fixed PINs.
Modern Methods: Secure Simple Pairing (SSP)
Introduced in Bluetooth 2.1, SSP significantly improved security and user experience. It offers several association methods:
- Numeric Comparison: Both devices display a 6-digit number. The user verifies they match. Simple and secure for devices with displays.
- Just Works: No user interaction required. Often used for simpler devices (like many headsets or speakers) that don’t have displays or keypads. While easy, it offers no protection against Man-in-the-Middle (MITM) attacks during the initial pairing if not combined with other security layers.
- Passkey Entry: One device displays a 6-digit number, and the user enters it on the other device. Similar to the old PIN method but within the more secure SSP framework.
- Out-of-Band (OOB): Uses another wireless technology, like Near Field Communication (NFC), to exchange pairing information securely. Tap your phone to an NFC-enabled speaker, and they pair instantly.
During this authentication phase, regardless of the method used, the devices exchange and derive cryptographic keys. The most important is the Link Key.
Step 5: Storing the Link Key (Bonding)
Once authentication is successful, both devices store the unique Link Key they’ve generated. This act of storing the key is called bonding. The Link Key serves as their shared secret. From now on, whenever these two specific devices connect, they use this stored Link Key to authenticate each other automatically and quickly, without needing to go through the full discovery and authentication process again.
The Link Key is typically stored in a secure area of the device’s memory, often linked to the Bluetooth address of the paired device.
Connecting After Pairing: It’s Faster!
Once bonded, connecting is much faster. When your phone’s Bluetooth is on and your earbuds are turned on, they perform a much quicker process called ‘connection.’ Your phone looks for devices it has previously bonded with (checking against stored Link Keys), and if it finds a known device (like your earbuds broadcasting their presence), they quickly establish a connection using the stored Link Key for authentication. No need for rediscovery or re-entering PINs.
Frequency Hopping After Connection
After a secure connection is established (paired or reconnected), Bluetooth devices employ Adaptive Frequency-Hopping Spread Spectrum (AFH). They rapidly switch between different frequencies within the 2.4 GHz band (1600 times per second!). This isn’t part of the *pairing* process itself but is crucial for maintaining a stable, interference-resistant connection *after* pairing/connecting. It helps them avoid interference from other devices using the 2.4 GHz band, like Wi-Fi networks or microwaves.

What Happens When You Unpair?
When you ‘unpair’ or ‘forget’ a device from your phone’s Bluetooth settings, you are essentially deleting the stored Link Key associated with that specific device’s Bluetooth address. The bonded relationship is broken. The next time you want to connect those two devices, they will have to go through the full pairing process again, starting with discovery mode.
FAQs About Bluetooth Pairing
Q: Why is my device not showing up when scanning?
A: The most common reason is that the device you’re trying to connect to isn’t in discoverable/pairing mode. Make sure its indicator light is flashing in the specific pattern that indicates pairing mode (not just on or connected). Also, ensure Bluetooth is enabled on the scanning device (your phone/computer) and they are within range.
Q: Why do I sometimes need a PIN and sometimes I don’t?
A: This depends on the Bluetooth version and the pairing method the devices use. Older devices might use Legacy Pairing with mandatory PINs. Newer devices typically use Secure Simple Pairing (SSP), which offers methods like “Just Works” (no PIN), “Numeric Comparison” (verify a displayed number), or “Passkey Entry” (enter a displayed PIN). Devices with no display usually default to “Just Works” or sometimes a fixed PIN.
Q: What is a Link Key and why is it important?
A: The Link Key is a shared secret generated during the pairing process. It’s a cryptographic key that allows two bonded devices to authenticate each other automatically and securely during subsequent connections. It’s crucial for maintaining a secure and hassle-free connection after the initial setup.
Q: Is Bluetooth pairing secure?
A: Modern Bluetooth pairing using Secure Simple Pairing (SSP) is generally considered secure against passive eavesdropping and common attacks, especially methods like Numeric Comparison or Passkey Entry. “Just Works” is less secure against active Man-in-the-Middle attacks during pairing itself, but connections *after* bonding (using the Link Key) are encrypted and secure. Always ensure your devices are using a recent Bluetooth version where possible.
Q: Why do I have to repair my devices sometimes?
A: This can happen for various reasons. Sometimes, one device might lose the stored Link Key (e.g., after a factory reset, firmware update, or a software glitch). Interference, distance, or trying to connect a device to too many other devices concurrently can also sometimes cause connection issues that are resolved by re-pairing.
Bringing It All Together
The next time your earbuds seamlessly connect to your phone, you’ll know it’s not just random chance. It’s the result of a clever, multi-step digital negotiation involving discovery, identification, secure authentication, and the creation of a unique shared secret – the Link Key. This invisible process ensures that your devices recognize their trusted partners, keeping your connections private, reliable, and hassle-free.
Understanding this process helps demystify those connection quirks and makes you appreciate the underlying technology that powers so much of our wireless world. Pretty cool, right?