Ever said something like, "My voice is my password," perhaps half-jokingly, only to wonder how that might actually function in the real world for security? It’s a fascinating concept, moving beyond *what* words you utter to focus intensely on *how* you deliver them.
Just like the unique swirling patterns on your fingertips form a fingerprint, your voice possesses equally distinct acoustic characteristics. Imagine your voice having its own signature, invisible but incredibly complex, carried simply on the airwaves. This is the essence of voice biometrics, often referred to as Voice ID or voiceprint analysis.
Before we dive deeper into the nuts and bolts of this technology, take a quick listen to our exploration of the topic in bite-sized form. We distilled the core concept into a YouTube Short:
Table of Contents
What Exactly is a Voiceprint?
The term "voiceprint" is a handy analogy, though not perfectly analogous to a fingerprint. While fingerprints are visual patterns, a voiceprint is a digital representation of the unique acoustic features of a person’s voice. It’s built from a multitude of characteristics that make your voice yours and yours alone. Think of it as a complex mathematical model or a unique spectral signature derived from the sound waves you produce.
These characteristics aren’t just about the words you say, but the underlying mechanics and habits of your speech:
- Pitch: The fundamental frequency of your vocal cords’ vibration.
- Rhythm: The timing, speed, and flow of your speech.
- Tone: The quality or timbre of your voice, influenced by the resonance in your vocal tract.
- Pronunciation: How you form specific sounds and articulate words.
- Accent and Dialect: Patterns specific to your regional or social background.
- Vocal Tract Geometry: The physical shape and size of your larynx, pharynx, nasal cavities, and mouth — these act like a unique resonating chamber for sound.
Because the physical aspects of your vocal tract are as unique as other physical features, and your learned speech habits are deeply ingrained, combining all these factors creates a highly distinctive pattern.
The Technology Behind the Recognition: From Sound to Science
So, how does a system capture these ephemeral sound waves and turn them into a digital signature it can recognize? It’s a multi-step process:
1. Audio Capture
It starts with a microphone converting sound waves into electrical signals. The quality of the microphone and the recording environment (minimal background noise is key) significantly impact the accuracy.
2. Feature Extraction
This is where the complex analysis begins. The raw audio signal is processed to identify and isolate the crucial acoustic features mentioned earlier. Advanced signal processing techniques are employed. One common method is using Mel-Frequency Cepstral Coefficients (MFCCs). MFCCs are a set of coefficients that collectively represent the short-term power spectrum of a sound, focusing on aspects relevant to human hearing. In simpler terms, the system breaks down the audio into tiny segments and analyzes the frequency distribution and energy within those segments over time.
3. Modeling
The extracted features are then used to create a mathematical model of the voice — the ‘voiceprint’. This model is essentially a set of parameters that statistically represent the unique characteristics of that specific voice. Machine learning algorithms, particularly those involving neural networks or Gaussian Mixture Models (GMMs), are often used to build these robust models during an enrollment process.
4. Storage
The resulting voiceprint model (a small data file, not the raw audio) is securely stored in a database, linked to the user’s identity.
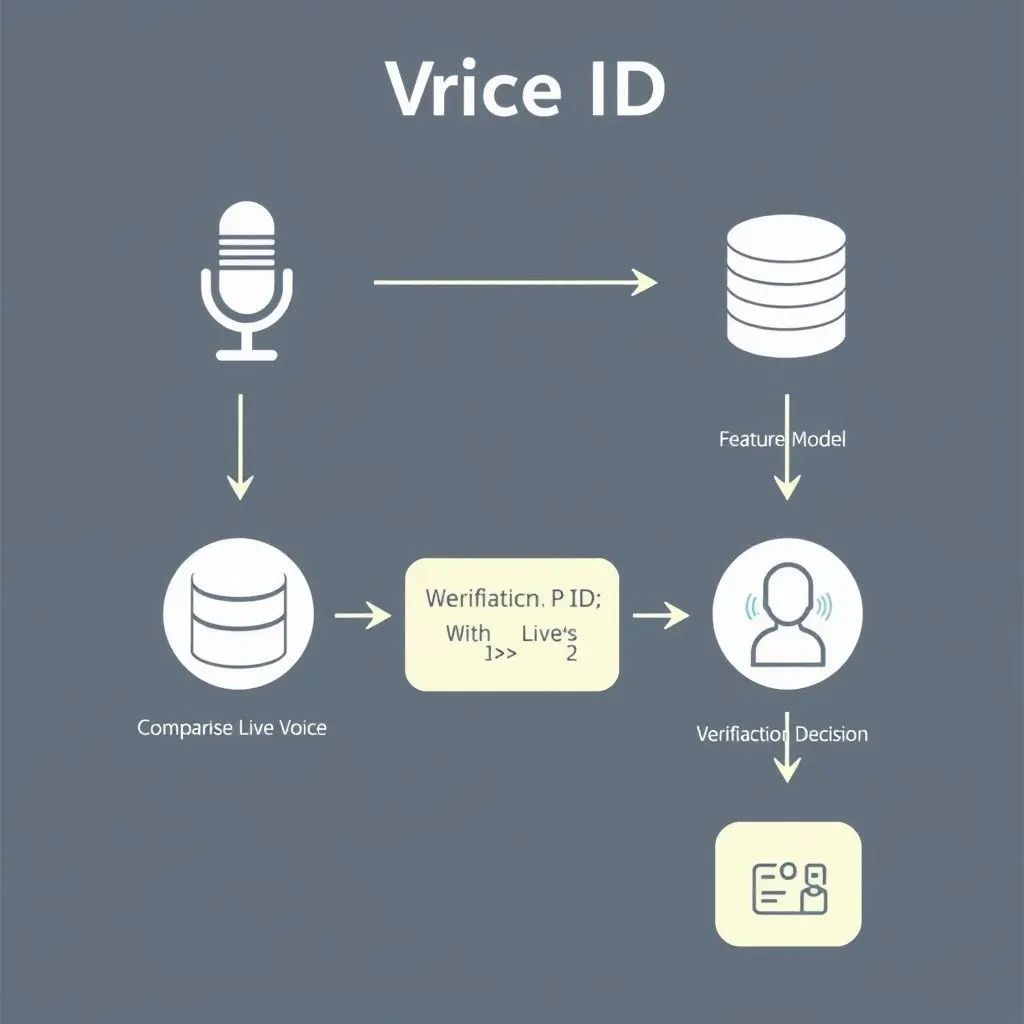
Creating Your Voiceprint: The Enrollment Process
Before a Voice ID system can verify you, it needs to know what your voice sounds like. This is the enrollment phase. Typically, you’ll be asked to repeat specific passphrases or speak naturally for a short duration. During this time, the system captures your voice, analyzes its unique acoustic patterns (as described above), and builds your initial voiceprint model. This model is then stored securely for future comparison.
The Verification Process: Proving It’s You
When you later interact with the system (e.g., calling a bank, unlocking an app), you’ll speak, often prompted to say a specific phrase again (text-dependent verification) or simply speak naturally (text-independent verification). The system captures this live audio, performs the same feature extraction process, and creates a temporary voice model. This temporary model is then compared against your stored voiceprint. A matching algorithm calculates a similarity score. If the score meets a predetermined threshold, the system authenticates you, granting access or confirming your identity.
Why is Voice ID Considered a Powerful Security Tool?
Voice biometrics offers compelling advantages in the security landscape:
- Uniqueness: As established, the combination of physical vocal tract characteristics and learned speech patterns makes each voice acoustically distinct.
- Difficulty of Replication: While simple voice recordings can be played back, they lack the liveness and subtle variations inherent in a live human voice. Advanced systems often incorporate "liveness detection" to spot recordings or synthesized speech by analyzing micro-fluctuations, background noise profiles, or even asking the user to say a random phrase. Replicating a voiceprint *perfectly* is incredibly challenging, far more so than guessing a password.
- Convenience: For users, it’s often easier and faster than typing passwords or answering security questions, especially in hands-free environments like phone calls.
- Passive Verification: In some scenarios, like call centers, verification can happen passively during a conversation without requiring the user to explicitly state a password.
Applications Where Voice ID Shines
Voice ID is finding its way into numerous sectors:
- Banking and Financial Services: For secure access to accounts via phone banking or mobile apps.
- Call Centers: Streamlining customer service by quickly verifying callers’ identities.
- Smart Assistants and IoT Devices: Personalizing experiences and controlling access based on recognized voices.
- Healthcare: Verifying patient identities for accessing records.
- Government and Enterprise Security: For internal system access or identity verification in various services.
Navigating the Challenges and Limitations
While powerful, Voice ID isn’t without its hurdles:
- Environmental Noise: High levels of background noise can make accurate capture and analysis difficult.
- Changes in Voice: Illness (like a cold or sore throat), aging, or emotional state can slightly alter voice characteristics, potentially affecting recognition.
- Microphone Quality: Variations in microphones (handsets, smartphone mics) can impact the quality of the audio input.
- Impersonation and Synthesis: While difficult, sophisticated voice synthesis and deepfakes are emerging threats, requiring robust liveness detection and ongoing algorithm improvements.
- Data Privacy: Storing voiceprint data requires strong security measures to protect against breaches.
- Enrollment Issues: A poor quality initial enrollment can lead to verification problems later.
Systems are constantly being improved to mitigate these issues through advanced algorithms, noise cancellation, and adaptive models that learn slight variations in a user’s voice over time.
Voice ID: How Does It Stack Up Against Other Biometrics?
Compared to fingerprints, facial recognition, or iris scans, Voice ID has pros and cons. It’s non-contact and can be used remotely (like over a phone call), which is a significant advantage. However, it can be more susceptible to environmental factors (noise) and transient user states (illness) than physical biometrics. It often works well as part of a multi-factor authentication system, combining the convenience of voice with another verification method for enhanced security.
Frequently Asked Questions About Voice ID
Here are some common questions people ask about this technology:
Q: Can someone fool a Voice ID system with a recording of my voice?
A: Basic systems might be vulnerable, but modern, secure Voice ID systems incorporate "liveness detection" technology specifically designed to detect recordings or synthesized speech. They analyze subtle cues that distinguish live speech from playback.
Q: What if I have a cold or my voice changes?
A: Most advanced systems are built with some tolerance for minor variations due to illness, environment, or emotion. They often use adaptive models that learn your voice over time. However, a severe change might require falling back to an alternative verification method.
Q: Is my actual voice recording stored?
A: No, typically only the voiceprint — the mathematical model of your voice’s unique characteristics — is stored. The raw audio recording is usually processed and then discarded, though policies can vary by provider.
Q: Is it accurate enough for high-security applications?
A: Voice ID accuracy has improved dramatically. While often used for convenience or as a primary factor in applications like call centers, for very high-security needs, it is frequently combined with other authentication methods (multi-factor authentication) for increased assurance.
Q: Can identical twins fool a Voice ID system?
A: Even identical twins have distinct voiceprints. While their vocal tracts might be physically similar, subtle differences in learned speech patterns, resonance, and even tiny anatomical variations usually result in distinguishable voiceprints that a well-trained system can differentiate.
Beyond the Mic
Voice ID represents a fascinating intersection of biometrics, signal processing, and machine learning. It leverages the incredible uniqueness of human speech to offer a convenient yet powerful layer of security. As the technology matures, becoming more resilient to noise, voice changes, and sophisticated spoofing attempts, we can expect to see it integrated into even more aspects of our digital and physical lives, making interactions smoother and more secure — all just by using the power of your voice.