Remember when our phones were, let’s be honest, glorified potato cameras? A fuzzy suggestion of reality was the best we could hope for. Fast forward to today, and that device in your pocket is a visual storytelling powerhouse, completely changing how we capture and share our lives. This leap didn’t just make things easier; it put a high-quality camera into nearly everyone’s hands, 24/7, transforming photography from a planned event into an everyday reflex.
This democratization of technology is incredible, but it also means our digital lives – full of precious memories and sensitive information – are more accessible, and thus, more vulnerable. Just as tech has evolved to empower us, we need our security measures to evolve too. That’s where the concept of layered defense comes in, and a critical layer for everyone is Two-Factor Authentication, or 2FA.
Speaking of how quickly tech evolves and brings cool new insights, we’ve got a little something that captures that spirit. It’s a quick visual byte that’ll make you nod in agreement (and maybe chuckle). Give it a watch, and then we’ll dive deep into how similar innovation is fortifying your digital world!
Table of Contents
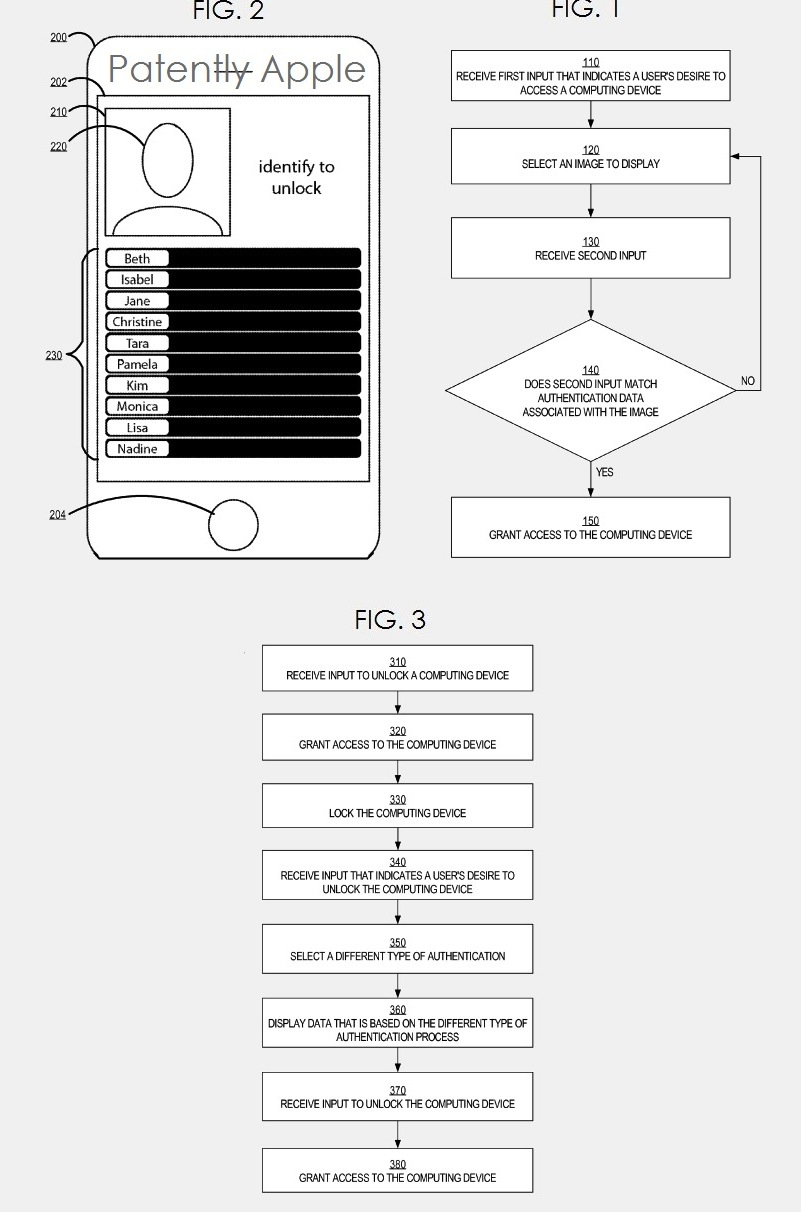
So, What Exactly is This Digital Double Lock? Understanding Authentication
Before we bolt the door twice, let’s talk about the first lock: authentication. In simple terms, authentication is the process of verifying that you are who you claim to be. Think of it as showing your ID to a bouncer at a club or using your key to open your front door. In the digital world, the most common form of authentication is the classic username and password combination.

Enter the Second Key: What is Two-Factor Authentication (2FA)?
Two-Factor Authentication (2FA), sometimes called two-step verification, adds a crucial second layer of security to your online accounts. It means that even if a cybercriminal gets hold of your password (the first “key”), they still can’t access your account without also possessing the second “key.”
Imagine your online account is a high-security vault. Your password unlocks the first heavy door. But with 2FA enabled, there’s a second, different lock right behind it, requiring a completely separate key. This significantly reduces the chances of an unauthorized breach.
2FA typically relies on combining two distinct types of credentials (or “factors”) from these categories:
- Something You Know: This is typically your password or a PIN.
- Something You Have: This is a physical item in your possession, like your smartphone (receiving a code via SMS or an authenticator app) or a dedicated hardware security key.
- Something You Are: This refers to biometric verification, like your fingerprint, facial recognition, or voiceprint. While often part of Multi-Factor Authentication (MFA), biometrics can serve as the second factor in a 2FA setup.
Why is 2FA Non-Negotiable in Today’s Digital Age?
Passwords, bless their cotton socks, are a bit like an old wooden screen door – easily kicked in. Here’s why relying solely on them is a risky game:
- Data Breaches: Massive data breaches are disturbingly common, often exposing millions of usernames and passwords. If you reuse passwords (a common mistake!), a breach on one site can compromise your accounts elsewhere.
- Weak Passwords: Many people still use simple, easily guessable passwords like “123456” or “password.”
- Phishing Attacks: Scammers are adept at creating fake login pages to trick you into revealing your credentials.
- Keyloggers & Malware: Malicious software can capture your keystrokes, including your passwords.

2FA is your digital bodyguard. By requiring that second factor, you make it exponentially harder for attackers to gain unauthorized access. Even if they have your password, they’d also need physical access to your phone or hardware token, or to somehow bypass your biometric scan – a much taller order.
How Does 2FA Work in Practice? The Nuts and Bolts
The process is usually quite straightforward:
- You log in: You enter your username and password on a website or app as usual (Factor 1: Something you know).
- The 2FA challenge: The service then prompts you for the second factor.
- You provide the second factor: This could be:
- Entering a 6-digit code sent to your phone via SMS.
- Entering a time-sensitive code generated by an authenticator app on your phone (e.g., Google Authenticator, Authy, Microsoft Authenticator).
- Plugging in a hardware security key and tapping it.
- Approving a push notification sent to your trusted device.
- Using a fingerprint or face scan.
(Factor 2: Something you have or Something you are).
- Access Granted: If both factors are verified, you’re in!
Decoding the Different Flavors of 2FA Methods
Not all 2FA methods are created equal in terms of security and convenience. Here’s a quick rundown:

- SMS-based 2FA: Codes are sent to your phone via text message.
Pros: Widely available, doesn’t require a smartphone app (just a phone that receives texts).
Cons: Vulnerable to SIM swapping attacks (where scammers trick your mobile carrier into transferring your number to their SIM card) and message interception. Generally considered the least secure of the common 2FA methods, but still better than no 2FA at all. - Authenticator Apps (TOTP – Time-based One-Time Password): Apps like Google Authenticator, Microsoft Authenticator, Authy, or Duo Mobile generate a new 6-8 digit code every 30-60 seconds.
Pros: More secure than SMS as codes are generated offline on your device and not transmitted over the mobile network. Many apps offer cloud backup of your 2FA accounts.
Cons: Requires a smartphone. If you lose your phone and don’t have backups, recovery can be tricky (always save your recovery codes!). - Hardware Security Keys (U2F/FIDO2): Physical USB, NFC, or Bluetooth Low Energy devices (e.g., YubiKey, Google Titan Key). You plug them in or tap them to authenticate.
Pros: Considered one of the most secure methods. Protects against phishing because the key authenticates with the legitimate site cryptographically. No codes to type.
Cons: You need to purchase the key and carry it with you. Not all services support hardware keys yet, though adoption is growing. - Push Notifications: Instead of a code, you receive a notification on a trusted device (usually your smartphone via an app like Duo or a platform’s own app). You simply tap “Approve” or “Deny.”
Pros: Very convenient and user-friendly.
Cons: Relies on the security of the device receiving the push and the app itself. Potential for “push fatigue” if users get too many requests and approve malicious ones by mistake. - Biometrics: Fingerprint scanners, facial recognition (like Face ID), or voice recognition can act as a second factor.
Pros: Very convenient, nothing to remember or type (beyond the initial password).
Cons: Security depends on the quality of the biometric scanner. Not all devices have robust biometric capabilities.
The Upsides and Downsides: Pros and Cons of 2FA
Like any security measure, 2FA has its advantages and potential drawbacks:
Pros:
- Dramatically Increased Security: This is the big one. 2FA makes it significantly harder for unauthorized users to access your accounts.
- Protection Against Common Attacks: Effective against phishing, credential stuffing, and brute-force attacks where passwords are the primary target.
- Peace of Mind: Knowing your important accounts have an extra layer of protection can be very reassuring.
Cons:
- Slight Inconvenience: It adds an extra step to the login process, which can feel a bit cumbersome initially.
- Reliance on a Second Device/Factor: If you lose your phone or hardware key and haven’t set up backup methods or saved recovery codes, you could be locked out of your account. This is why saving recovery codes in a safe place is paramount!
- Not All Methods Are Equal: As discussed, SMS is less secure than authenticator apps or hardware keys.
Getting Started: How to Enable 2FA
Enabling 2FA is generally straightforward. You’ll usually find the option in the security settings or account settings section of your online services (email, social media, banking, cloud storage, etc.).
- Look for terms like “Two-Factor Authentication,” “2-Step Verification,” or “Login Verification.”
- Follow the on-screen instructions. You’ll typically be asked to choose your preferred 2FA method.
- Crucially, if offered, save your recovery codes! These are one-time codes you can use to access your account if you lose your second factor. Store them offline in a very safe place (e.g., printed out and stored securely, or in a password manager).
Disclaimer: The exact steps for enabling 2FA vary from service to service. Always consult the official help documentation or support pages for the specific platform you are using.

Frequently Asked Questions (FAQs) About 2FA
- Is 2FA completely foolproof?
- No security measure is 100% foolproof. Highly sophisticated attackers can sometimes find ways around 2FA (e.g., through advanced social engineering or exploiting vulnerabilities in specific 2FA implementations). However, for the vast majority of users and against common threats, 2FA significantly boosts your security.
- What if I lose my phone or my 2FA device?
- This is why recovery codes are vital. Most services provide a set of backup codes when you enable 2FA. Store these securely and separately from your primary 2FA device. Some authenticator apps also offer backup and sync options. For hardware keys, you might register a backup key.
- Is SMS-based 2FA better than nothing?
- Absolutely. While it’s the least secure of the common methods, it’s still a significant improvement over just a password. If SMS is the only option offered, use it. But if an authenticator app or hardware key support is available, prefer those.
- Can I use 2FA for all my online accounts?
- Most major online services (email providers, banks, social media platforms, password managers, cloud storage) now offer 2FA. It’s becoming increasingly standard. Always check the security settings of your important accounts.
- Does 2FA make me immune to phishing?
- It makes you much more resistant, especially if you use hardware keys (which can verify the website’s authenticity). However, you still need to be vigilant. If a phishing site tricks you into entering your password AND your 2FA code quickly, they might be able to use it. The key is that they need both, and the 2FA code is usually time-sensitive or one-time use.
Bolstering Your Digital Defenses: The Path Forward
In a world where our digital identities are as valuable as our physical ones, relying on a single password is like leaving your front door ajar. Two-Factor Authentication isn’t just a fancy tech term; it’s an essential practice for anyone who values their online security and privacy. It’s the digital equivalent of adding a deadbolt to your screen door – a simple step that makes a world of difference.
While the security landscape constantly evolves, with Multi-Factor Authentication (MFA – using more than two factors) and passwordless solutions like passkeys gaining traction, 2FA is the robust, accessible standard you should implement today.
Take a few minutes to review your critical online accounts. If you haven’t enabled 2FA, make it a priority. Your future self, safe from the headaches of a compromised account, will thank you.