Ever felt like you’re navigating a vast digital ocean, teeming with wonders and… well, some rather sneaky anglers? These aren’t your typical fishermen hoping for a prize tuna. No, these cyber-anglers are “phishing” – with a ‘ph’ – and their catch of the day could be your sensitive information. They cast out tempting lures, hoping you’ll bite. But what exactly is this digital fishing expedition all about, and how can you avoid becoming their next catch?
Table of Contents
What Exactly is Phishing? The Art of the Digital Deception
Phishing is a cunning form of cybercrime where attackers impersonate legitimate individuals, trusted companies, or even government agencies. Their goal? To trick unsuspecting victims into divulging valuable personal data. This could be anything from your login credentials (usernames and passwords) and credit card numbers to bank account details or your Social Security number.
The metaphor of fishing is incredibly apt. Imagine the scammer as a patient fisherman. They meticulously craft their ‘bait’ – a cleverly designed email that looks like it’s from your bank, a text message about a package delivery, or an urgent pop-up warning about a security issue. This bait is dangled on a ‘line’ (the email, SMS, or website) and cast out into the vast digital waters. They’re waiting for someone to mistake the lure for a genuine opportunity or a critical warning and ‘bite’ by clicking a malicious link, downloading infected software, or providing their confidential details.

The Phisherman’s Tackle Box: Common Types of Phishing Lures
Phishing isn’t a one-size-fits-all scam. Attackers have a diverse tackle box filled with various techniques to suit different targets and situations. Here are some of the most common types you might encounter:
Email Phishing: The Classic Cast
This is the most prevalent form. Scammers send out mass emails that appear to come from legitimate sources like banks, e-commerce sites, or tech companies. These emails often create a sense of urgency or curiosity to prompt immediate action.
Spear Phishing: Personalized Bait for a Bigger Catch
Unlike broad email phishing, spear phishing is highly targeted. Attackers research their victims (individuals or specific employees within an organization) and craft messages tailored to them, using personal information to make the lure more convincing. This makes spear phishing particularly dangerous and effective.
Whaling: Hunting for the Giants
Whaling is a type of spear phishing aimed at high-profile targets like CEOs, CFOs, or other senior executives. The goal is to trick these “big fish” into authorizing large wire transfers or revealing confidential company strategy, as they have access to more valuable assets and information.
Smishing (SMS Phishing): Text-Based Traps
As the name suggests, smishing uses text messages (SMS) instead of emails. You might receive a text with an urgent alert about a bank account, a prize notification, or a fake delivery update, complete with a link to a fraudulent website.
Vishing (Voice Phishing): The Deceptive Call
Vishing involves voice communication. Scammers might call you pretending to be from tech support, your bank, or even a government agency like the IRS. They use persuasive language and often create a sense of panic to extract information over the phone.
Pharming: Poisoning the Digital Well
Pharming is a more sophisticated technique where attackers redirect users from a legitimate website to a fake one by compromising DNS (Domain Name System) servers or a user’s host file. Even if you type the correct web address, you might land on a fraudulent site designed to steal your credentials.
Angler Phishing: Social Media Snags
This type of phishing occurs on social media platforms. Scammers might create fake customer support accounts for well-known brands or send direct messages with malicious links, preying on users seeking help or engaging with companies online.
Don’t Get Reeled In! Spotting the Shiny, Deceptive Lure
While phishers are getting craftier, their lures often have tell-tale signs. Keep an eye out for these red flags:
- Urgent Calls to Action: Phrases like “Immediate action required,” “Your account will be suspended,” or “Verify your details within 24 hours” are designed to make you panic and act without thinking.
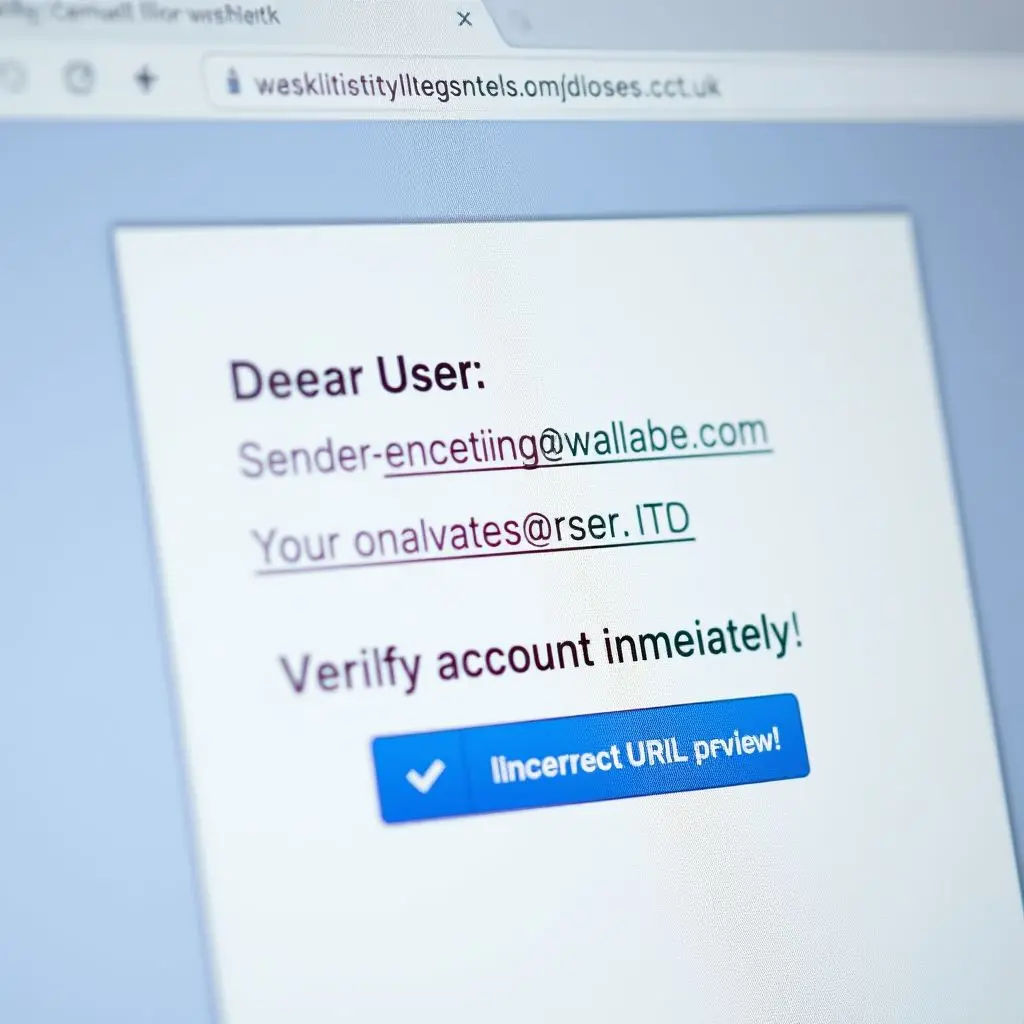
- Generic Greetings: Emails starting with “Dear Valued Customer,” “Dear User,” or just your email address instead of your name can be a sign. Legitimate companies usually personalize their communications.
- Poor Grammar and Spelling: While some scammers are sophisticated, many phishing emails are riddled with grammatical errors, awkward phrasing, or spelling mistakes.
- Suspicious Links and Attachments: Always hover your mouse cursor over links before clicking to see the actual destination URL. If it looks different from what’s displayed or seems unrelated, don’t click. Be extremely wary of unsolicited attachments, especially .exe, .zip, or .scr files.
- Requests for Sensitive Information: Legitimate organizations will rarely ask you to provide passwords, full bank account numbers, or Social Security numbers via email or text.
- Mismatched Email Addresses or Sender Details: Check the sender’s email address carefully. Phishers often use addresses that are slightly altered versions of legitimate ones (e.g., `[email protected]` instead of `[email protected]`).
- Too Good To Be True Offers: If an email or message promises you a large sum of money, an expensive prize for a contest you never entered, or an unbelievable discount, it’s almost certainly a scam. Remember, if it sounds too good to be true, it probably is.
See The Bait in Action: A Quick Bite on Phishing
Feeling a bit overwhelmed by all these sneaky tactics? Sometimes a quick visual is the best way to see how these phishers operate. We put together a short, snappy video that illustrates this whole “digital fishing” concept perfectly, just like the voiceover that inspired this post. If you’ve ever wondered what a phishing lure looks like in action, give this a watch – it might just help you spot the next one trying to reel you in!
The Cost of a Nibble: Consequences of Falling for Phishing
Taking the bait might seem like a small click, but the consequences can be severe and far-reaching:
- Identity Theft: Scammers can use your personal information to open new accounts, take out loans, or commit other fraudulent activities in your name.
- Financial Loss: Direct theft from bank accounts, unauthorized credit card charges, or being tricked into making fraudulent payments.
- Malware Infection: Clicking malicious links or downloading compromised attachments can install ransomware, spyware, or viruses on your device, leading to data loss or further compromise.
- Reputation Damage: For businesses, a successful phishing attack can lead to data breaches, loss of customer trust, and significant reputational harm.
- Loss of Access to Accounts: Scammers can lock you out of your email, social media, or financial accounts.
Navigating Safely: How to Avoid the Phisherman’s Hook
The good news is that with a little vigilance and knowledge, you can significantly reduce your chances of getting hooked. Here’s how to stay safe in phishy waters:
- Be Skeptical: Treat unsolicited emails, texts, and calls with caution, especially if they ask for personal information or urge immediate action.
- Verify Independently: If you receive a suspicious message from a company, don’t click links or call numbers in the message. Instead, go directly to their official website by typing the address in your browser or use a known contact number to verify the communication.
- Use Strong, Unique Passwords and Multi-Factor Authentication (MFA): Create complex passwords for all your accounts and enable MFA wherever possible. This adds an extra layer of security even if your password gets compromised.
- Keep Software Updated: Regularly update your operating system, web browser, and security software. Updates often include patches for security vulnerabilities that phishers exploit.
- Educate Yourself and Others: Stay informed about the latest phishing tactics. Share your knowledge with friends, family, and colleagues.
- Use Security Software: Install reputable antivirus and anti-malware software and keep it updated. Many email providers also have built-in phishing filters.
- Think Before You Click: This is the golden rule. Take a moment to analyze the message before taking any action.

Hooked! What to Do If You Took the Bait
If you suspect you’ve fallen victim to a phishing scam, act quickly:
- Change Your Passwords: Immediately change the passwords for any accounts you believe might be compromised, starting with the one targeted in the phishing attempt. If you use the same password elsewhere (a bad practice!), change those too.
- Notify Relevant Institutions: Contact your bank, credit card company, or any other organization involved to report the incident and check for fraudulent activity. They can help you secure your accounts.
- Scan Your Devices: Run a full scan with your security software to check for malware.
- Report the Phishing Attempt: Report the phishing email or message to the impersonated company and relevant authorities (e.g., the Anti-Phishing Working Group (APWG) or the Federal Trade Commission (FTC) in the US).
- Monitor Your Accounts: Keep a close eye on your bank statements, credit reports, and online accounts for any suspicious activity.
Frequently Asked Questions (FAQs) About Phishing
Can I get phished just by opening an email?
Generally, just opening a phishing email is unlikely to cause harm, especially if your email client doesn’t automatically download images or run scripts. The real danger lies in clicking malicious links, downloading attachments, or replying with sensitive information. However, some sophisticated attacks might try to exploit vulnerabilities in email clients, so keeping your software updated is crucial.
Are phishing attacks always easy to spot?
No, unfortunately. While many phishing attempts have obvious red flags, some are incredibly sophisticated and can look identical to legitimate communications. Spear phishing attacks, in particular, can be very convincing due to their personalized nature.
Do legitimate companies ask for sensitive information via email?
Reputable companies, especially financial institutions, will almost never ask you to provide your password, full account number, PIN, or other highly sensitive data via email, text, or unsolicited call. If you receive such a request, treat it as a major red flag.
What’s the difference between phishing and spam?
Spam is unsolicited bulk email, often commercial in nature (like advertisements). While annoying, spam isn’t always malicious. Phishing, on the other hand, is a type of spam that is specifically designed to deceive you into revealing sensitive information or installing malware. All phishing is spam, but not all spam is phishing.
Stay Alert, Stay Safe: Don’t Be Today’s Catch
The digital ocean is vast and wonderful, but it’s also home to those wily phishermen. By understanding their tactics, recognizing their lures, and practicing safe online habits, you can navigate these waters confidently without getting hooked. Remember, the best defense against phishing is a healthy dose of skepticism and a keen eye for anything that looks remotely… well, fishy.
Did this guide help you understand the murky world of phishing? Share your own experiences or tips for spotting scams in the comments below – let’s help each other stay safe out there!